
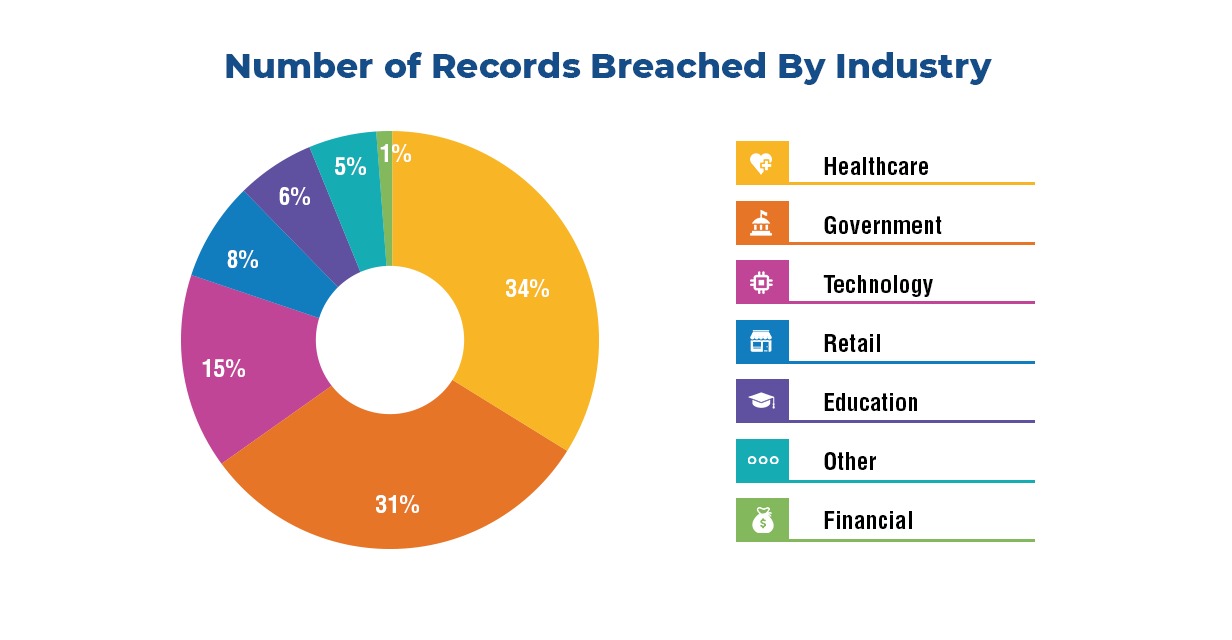
In India the Healthcare sector spends a top line of 1 -5% of their budget on their IT security. Compare this with the banking and financial sector that budgets for a whopping 15 -20% of their annual IT spend on data security. Cybersecurity in healthcare in India becomes even more a priority with the National Digital Health Mission that will connect all patient health records.
The pandemic and lockdowns that followed saw a 500% increase in patients opting for online consultations with doctors. Patient Electronic Health Records (EHR) are often shared through insecure networks with multiple user access. These can be susceptible to cybercriminals and be compromised through malware. Information stored in health care institutions is not just patient health data but also medical insurance and billing information and this has high value in the black market.
Healthcare cybersecurity strategies to protect data
July 15th, 2019 and the hospital receptionist at MGM Hospital in Mumbai came in to work and started her computer but was not able to login. When hospital system administrator Amit Vavhal tried to get into the system to check her complaint, he was stunned by the message he read on the screen. The attacker’s message read that they had encrypted all the data and the hospital would have to pay them in bitcoin for decryption. While a cybercrime was filed, all processes were switched to manual paperwork, including billing, while scheduled operations had to be cancelled.
55% of healthcare companies in the US alone have faced cyberattacks, the data for India is not known. Here are the top 5 ways to ensure information security in healthcare to prevent cyberattacks and security breaches.
1. Identify and plug threat entry points
A threat entry point can be any vulnerability in your system that can be used by a hacker to insert a malware into the network or even access critical data without being detected. Many medical software can connect to other applications and vendor networks and might even be still connected to legacy systems. Most organisations,not just the healthcare industry, have no comprehensive understanding of their hybrid networks with no overview of vulnerable access points or ability to identify access policy violations.
This,then is the first step in ensuring healthcare cybersecurity – create an accurate inventory of all applications, servers, objects and networks that are talking to each other. This can identify any access routes that are noncompliant with access regulation policy. It might even throw up forgotten servers that can still access the network and could be vulnerable threat entry points.
Also read: NDHM – set to transform India’s healthcare through technology
2. Implement multilayer defence system
Patient information and billing information is 10 times more valuable than just credit numbers. A credit card fraud is usually detected within days while health information theft can go undetected for years.
This is the reason a multilayered approach for healthcare security is a necessity. A multi-layered defence inserts multiple steps before someone can access data. This can be up to a 7 layered defence and a few of the layers are
Network security using SSL, advanced firewall configuration, VPN security and intrusion detection and prevention. This layer needs to be constantly updated.
Data encryption at rest and in transit, two-factor authentication and malware protection. Frequent patches or upgrades can make this layer vulnerable
Server-side file integrity monitoring along with role-based access controls.
Mobile and medical devices are often the Achilles heel because these outside devices are out of the secured network
3. Protect data on medical SMART devices

Protecting MIoT requires a concerted strategy for information security in healthcare
Identify and monitor all connected medical devices for anomalous behaviour. When thousands of medical devices are in the network this requires intelligent cybersecurity solutions to detect a data breach.
Segment MIoT based on vulnerability. Also, evaluate creating an isolated network for connected devices using VLANS and firewall technology.
Ensure regular software patching and firmware updates, prioritizing by individual risk profile of medical device groups.
Also read: EHR vs EMR. Why the difference is important in healthcare
4. Train staff on security protocol
The weakest link in healthcare are the users that are accessing different parts of the healthcare digital system. Even with strong firewalls and other defences, human error can cause breach in the best defence through downloading unauthorized software, weak passwords or opening phishing emails.
There must be regular training sessions on updated security protocols and it can also be customized for different employee groups.
5. Ensure vendors are also compliant
Insurance companies, healthcare business partners and even your information technology partners should have clean security records to protect medical information. Any vulnerability in the supply chain can drastically increase the security risk of healthcare data. Every organisation must have a cybersecurity compliance framework that outlines the steps to manage every aspect of the vendor relationship.
Finally, inspite of having all preventive measures in place it is still possible to fall victim to a cyberattack. It is crucial to establish a comprehensive data breach response plan to allow the security team to quickly respond to a breach and reduce downtime to the best extent possible.
At iTech India, we have an in-depth experience in the health sector and understand the unique challenges involved. We are the trusted technology partners for many American health care providers and can help you get the most out of your secured EHR solutions.






