In the ever-changing cyber security threats landscape, cybercrime will cost the world $6 trillion by the end of 2021. This number will rise to $10.5 trillion by 2025. The constant barrage of headlines about corporate data breaches makes us aware of the vulnerability of our data in a digitally connected world.
The problem is that individuals and organizations can get complacent if they believe in the not-always-accurate cybersecurity myths and get a rude awakening when their data is compromised. Myths slow down the adoption of best practices and are damaging to not just the brand image but also their bottom line. Here are the top 10 cybersecurity myths that could be putting your organization at huge risk.
Myth 1: I’ll know right away if any of my systems get affected
This would have been accurate over a decade ago when viruses would cause your computer to slow down, load pop-ups, and other issues. Today’s malware, on the other hand, is quite subtle. They now take their time to surface, progressively compromising your device while everything else continues to function normally. This allows the virus to gain access to your files and wreak substantial damage before being noticed.
Modern ERP systems use one centralized database or integrated layers that connect to different databases (HR systems, CRM, Products, etc) to provide unified data access and visibility. . The big benefits it provides are also the reason why ERP solutions are the prime targets for cybercriminals. Last year saw a record number of ransomware and cyberattacks on small and medium businesses. Remote working, further, threw up gaps in security systems that made them vulnerable targets.
It is critical that all laptops and mobile devices accessing organization systems have reputable anti-virus software. It is just as important to be aware that out-of-date software is a high risk. Ensure security patches are upgraded, always have a double-authentication system, and have an updated disaster recovery plan.
Also read: If You’ve No Website Security, Here’s Why Hackers Want You
Myth 2: My advanced cyber security software will take care
Many consumers believe that cyber security software will protect their data from hackers. Yet, FireEye, a top cybersecurity firm was one of the organizations hacked in 2021 by a ‘nation-state’, hinting at Russian involvement. The $3.5 billion company responsible for identifying cybersecurity breaches for global companies like Sony, were themselves hacked. If it can happen to them, what chance have smaller businesses?
What businesses must do is to make it as difficult as possible for a cyber security breach to occur and if it does, be able to recover as fast as possible. Security tools and solutions are only as good as their configuration, monitoring, maintenance, and integration with overall security operations. As already mentioned, out-of-date ERP systems will not be able to keep up with the latest compliance regulations.
If you can’t prevent all attacks, your security system should at least try to limit the harm. Software is only the first step in a comprehensive cybersecurity strategy. To truly safeguard your business, you’ll need a comprehensive business continuity and data recovery plan.
An interesting read: 7 Legacy System Modernization Approaches, Which One Works Best for Your Business?
Myth 3: We have strong passwords
A strong, unique password for each of your accounts is essential for data security, but even the most secure password can be hacked or cracked. To make it difficult for hackers, you’ll need an extra layer of security, such as two-factor or multi-factor authentication for additional barriers before allowing access.
Cyber security tip: Use a unique local administrator account that automates the process of updating the passwords for all local administrator accounts on your network and stores the information in a database. Additionally, you can turn off NBNS and LLMNR to prevent spoofing attacks.
In reality, one of the most important aspects of cybersecurity readiness that businesses ignore is what information is available in the first place, rather than how individuals get it. According to a recent study, 41% of organizations have at least 1,000 sensitive files available to all employees. Many businesses also lack a strategy for monitoring admin access. Strong passwords help keep your firm safe, but once a malicious intruder is in the system, there’s a lot more at risk.
Myth 4: No hacker will be interested in my business
Going by Verizon’s 2019 Data Breach Investigations Report, small business cyber security breaches accounted for 43% of overall breaches. They become targets because small firms’ cybersecurity is mostly weaker than that of major organizations.
Hackers are using automated tools to find vulnerabilities. Their program does all of the work for them, and it does it swiftly and effectively. They can begin exploiting a flaw after a vulnerability has been identified.
Cybercriminals don’t care whose system they’re exploiting as long as there’s money to be made.
Regardless of how many people you have or how much money you make each year, you must anticipate that you will be the target of a cyberattack and plan accordingly. Another point to consider is that businesses of all sizes hold information that should not be made public or get into the hands of hackers. There’s a hacker out there who might be interested in confidential customer information or commercial secrets.
Myth 5: My IT Department will tackle it
Normally, it is the responsibility of the IT department to implement and review policies, but they cannot handle everything. When it comes to cybersecurity, each employee bears some responsibility. Employees who aren’t properly trained are more likely to download malware via emails or hazardous websites.
There should be clear policies and easy-to-understand training when it comes to cyber security threats. If your employees aren’t properly taught, they may unwittingly expose your company to threats.
Myth 6: Personal devices don’t need any additional security
Employees usually believe that the security protocols that apply to the company’s computers do not apply to their personal devices. As a result, while Bring Your Own Device (BYOD) are a cost-effective strategy, they have exposed businesses to cyber dangers. Employees who use their own devices for work-related purposes must adhere to the same security rules as the rest of the network’s machines. These guidelines do not apply only to cell phones and PCs. BYOD regulations should apply to any internet-connected devices, including wearables and IoT devices to prevent cyber security threats.
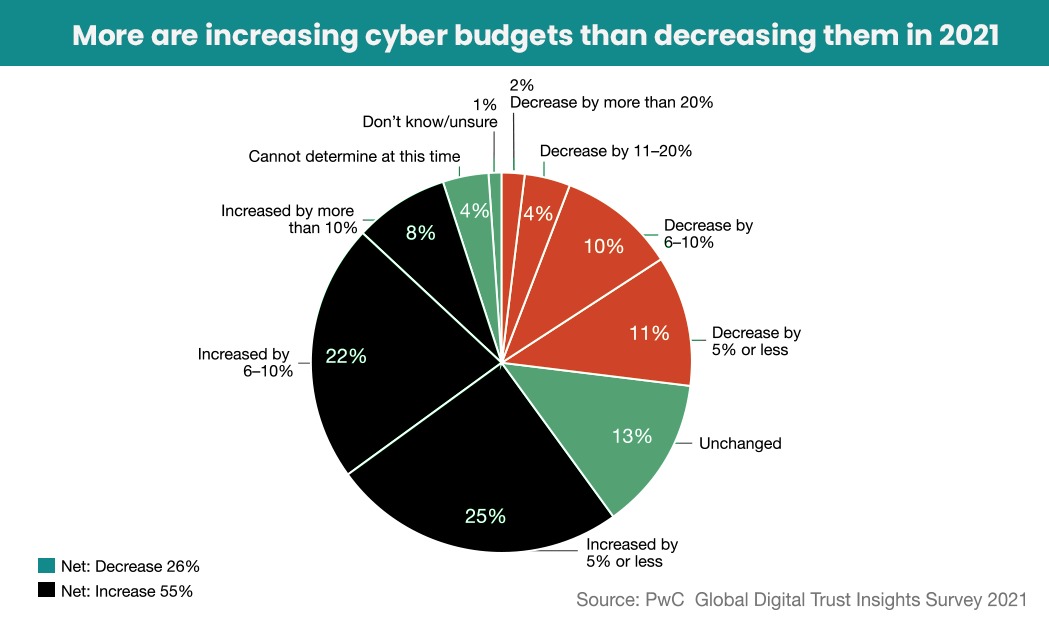
Myth 7: I don’t have the budget for it
Oftentimes, if funding becomes tight, cybersecurity may be pushed to the bottom of the priority list. Examining the consequences of a cybersecurity attack is a simple way to disprove this notion.
SMBs have a 50/50 probability of being hacked. Aside from that, the financial consequences of a successful attack might cripple or bankrupt your firm. Given these facts, the best cost-effective option will always be to invest in cybersecurity projects.
However, spending more on cyber security does not necessarily mean spending it on the right cyber tools. A successful cybersecurity strategy depends on how the budget is allocated. Cyber threats cannot be handled through manual processes alone. Does your organization have AI systems are trained on large data sets to spot cyber threats and any malicious activity?
Myth 8: It is enough if we comply with all industry regulations
Adhering to compliance regulations such as the Health Insurance Portability and Accountability Act (HIPAA) , GDPR, or Payment Card Industry (PCI), for example, is essential for conducting business, building trust, avoiding legal ramifications, and securing sensitive data. Simply meeting these requirements does not equate to an effective cybersecurity strategy for an enterprise, it needs to go beyond.
To manage cybersecurity risk, use a solid framework like the NIST Cybersecurity Framework (US. Department of Commerce). Keep yourself abreast with the latest details and best practices about the National Institute of Standards and Technology’s Cybersecurity Framework.
Myth 9: We conduct regular penetration tests
Many firms believe that by conducting frequent penetration tests, they can avoid cybersecurity problems. A penetration test is ineffective unless the organization can manage and fix the vulnerabilities and security flaws uncovered during the test.
Furthermore, the company should think about the test’s scope, such as whether it covers the entire network and enables for accurate replication of the typical cyber threats. Most organizations look at the test’s scope from the organization’s own perspective. It should also take an outside-in view, from the vantage point of an attacker.
Myth 10: Only external factors cause cyber issues
While external threats are clearly a worry and should be properly monitored, insider threats are equally deadly. Insider threats are responsible for up to 75% of data breach incidents, according to a study by Security Intelligence.
Insider risks can come from disgruntled employees seeking professional vengeance to unaware colleagues lacking sufficient cybersecurity training. OFtentimes something as simple as emailing critical information to the wrong person can be a security breach.
Performing enterprise-wide risk assessments to tackle security challenges with regards to their priority, enforcing strict and consistent policies and documentation, enabling strict surveillance, monitoring remote access from all endpoints, and using a log correlation engine to monitor and audit employee actions are some of the top ways to prevent insider attacks and safeguard your business operations.
Finally
Cybersecurity is a never-ending war against unseen forces. Many emerging, highly secure technologies such as AI and Machine Learning are helping to secure organizational data. The new entrant to this space is blockchain technology. All records in a blockchain are secured through cryptography and network participants have their own private keys for transactions. Since Blockchain data is decentralized, and information cannot be changed from a single computer, making it tamper-proof.
To know more about making your ERP systems secure, speak to our experts.