In today’s digital world, organizations across the globe are striving to enhance their cybersecurity and data privacy standards. To this end, iTech is thrilled to announce that we have recently attained two crucial certifications: Service Organization Controls (SOC 2 Compliance) and ISO 27701. These certifications represent a significant milestone in our commitment to ensuring the utmost levels of security and data privacy for our clients.
iTech India, with its office in Dallas, Texas, and a state-of-the-art development center in Chennai, India, is a pioneering technology company that specializes in cutting-edge AI solutions for our clients. Our comprehensive services encompass software development, IT consulting, digital transformation, and Proprietary Products like RehabONE EHR platform and DocExtract (AI-powered document processing). iTech India’s team comprises highly skilled professionals and subject matter experts proficient in a wide spectrum of technology stacks.
Service Organization Control (SOC 2) Certification
SOC, or Service Organization Controls, has its roots in the American Institute of Certified Public Accountants (AICPA) and is a comprehensive examination of a service organization’s internal controls and processes. The AICPA developed the SOC framework to enhance trust and transparency in service organizations by providing valuable insights into their control environments. The framework assesses the design and effectiveness of controls related to security, availability, processing integrity, confidentiality, and privacy of data.
The “2” in SOC 2 Compliance indicates the specific type of SOC report being issued.
SOC 2 certification holds immense significance in the tech and service sectors as it validates an organization’s commitment to safeguarding its clients’ data. It assures clients that stringent internal controls are in place to protect their sensitive information, fostering trust in the service provider.
SOC 2 reports are relevant in situations where a service organization hosts customer data and the security and privacy of that data are critical concerns.
SOC 2 compliance revolves around five key principles, known as Trust Service Categories (TSCs): security, availability, processing integrity, confidentiality, and privacy.
Process to Obtain SOC 2 Certification:
A SOC 2 certification represents an external audit report conducted by independent auditors.
Obtaining SOC 2 certification is no small feat and involves several key steps:
- Planning and Engagement: The process begins with the organization planning the examination and engaging a qualified independent auditor.
- Control Identification: The organization identifies the controls relevant to the engagement and ensures they are appropriately designed to address the defined criteria.
- Control Testing: The auditor conducts testing to determine the effectiveness of these controls and assess their design and operation.
- Report Preparation: Following the testing, the auditor compiles a detailed SOC report, summarizing the findings, and describes the organization’s control environment.
- Client Distribution: The organization then shares this report with its clients and, based on the examination’s results, ensures that necessary improvements are implemented.
It’s important to note that SOC 2 Compliance isn’t universal. It’s typically attained by organizations operating in sectors where data security and control standards are of paramount importance, such as technology, finance, and healthcare.
SOC 2 certification demonstrates the commitment of iTech to meeting rigorous data security standards, making it a valuable asset for our clients. It provides transparency, reduces security risks, and ensures compliance with industry regulations, instilling confidence in the security of client data.
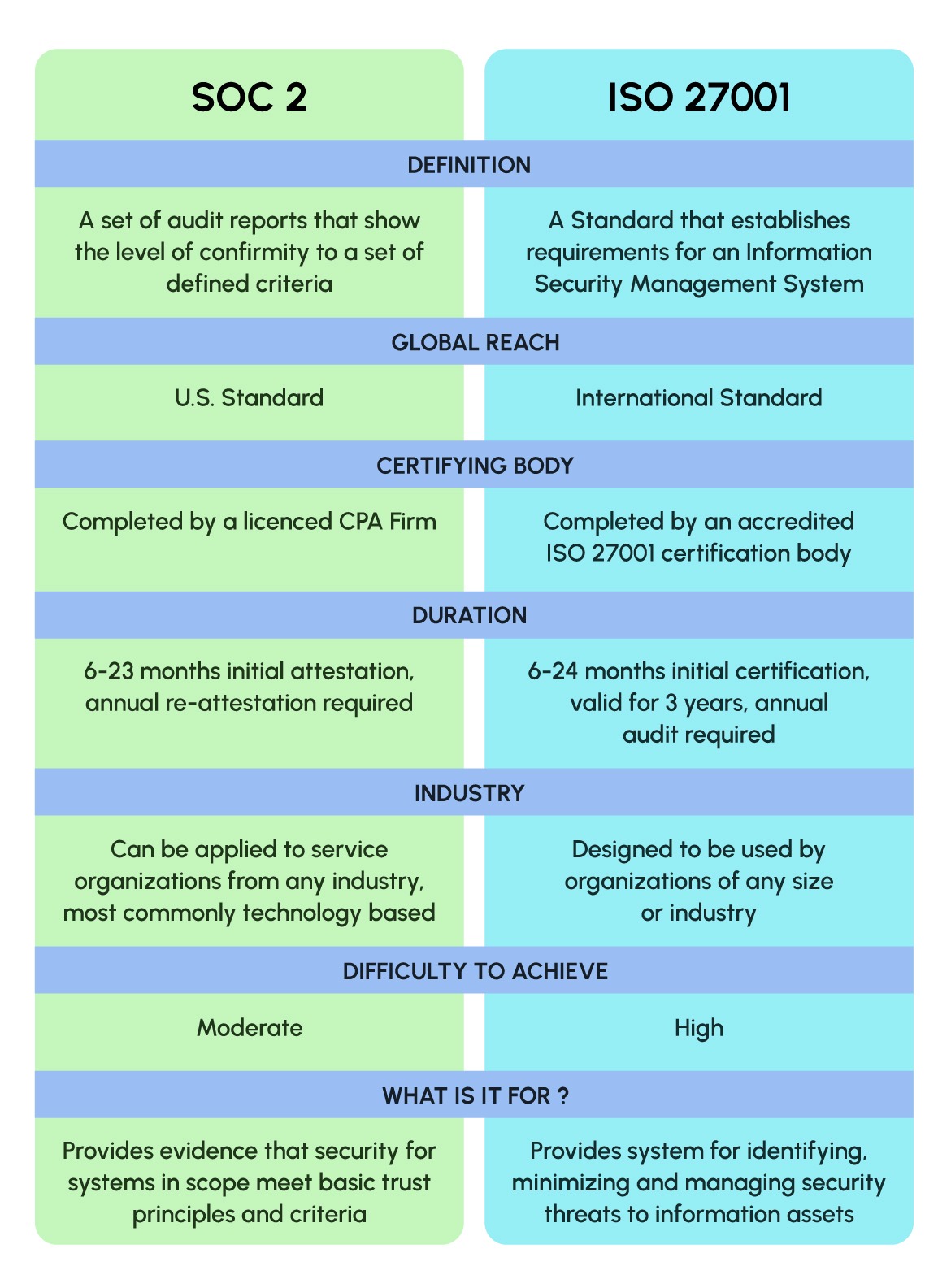
ISO 27701 Certification as an extension of ISO 27001
ISO 27701 is an extension of the ISO 27001 standard, which is a globally recognized framework for information security management. Both standards are essential because they cover different dimensions of security. ISO 27001 safeguards data against general security threats, while ISO 27701 specializes in privacy protection, ensuring compliance with privacy laws and addressing data privacy concerns, which have become increasingly significant in today’s data-centric world..
The International Organization for Standardization (ISO) developed ISO 27701 in response to the increasing global concern for data privacy. With the proliferation of data breaches and privacy scandals, ISO 27701 was designed to provide a standardized approach to managing privacy, helping organizations secure personal information and protect individuals’ privacy rights.
Process to Obtain ISO 27701 Certification:
ISO 27701 sets out requirements and guidelines for establishing, implementing, maintaining, and continually improving a Privacy Information Management System (PIMS).Achieving ISO 27701 certification requires a structured approach:
- Scoping: The organization defines the scope of its PIMS, specifying which areas it covers and the relevant privacy requirements.
- Risk Assessment: An in-depth risk assessment is conducted to identify potential privacy risks and their impact.
- Policy Development: The organization develops privacy policies, procedures, and controls based on the identified risks and requirements.
- Implementation: These policies and controls are implemented throughout the organization, with an emphasis on privacy by design.
- Auditing and Certification: An accredited certification body audits the organization’s PIMS to ensure compliance with ISO 27701. If successful, certification is granted.
ISO 27701 certification underlines iTech’s commitment to safeguarding our clients’ privacy and personal information. It provides clients with the assurance that their data is handled in compliance with legal requirements, which is particularly vital in an era of stringent data protection regulations like the GDPR and HIPAA for which iTech is also certified. Moreover, iTech’s ISO 27701 certification can become a powerful competitive advantage for our clients as they demonstrate their dedication to data privacy and security.
Why Technology Service Providers Pursue Both SOC and ISO 27701
While SOC 2 certification is widely recognized in the United States, ISO 27701 holds global recognition. Technology service providers like iTech who operate in America and internationally get both SOC 2 and ISO 27701 to demonstrate their commitment to global data privacy standards.
SOC 2 compliance provides assurance regarding the overall control environment of a service organization, including data security and privacy controls. ISO 27701, on the other hand, focuses specifically on privacy management. By obtaining both certifications, technology service providers ensure comprehensive coverage of security, availability, processing integrity, confidentiality, and privacy aspects.
Many clients, especially in industries where data security and privacy are paramount, may require service providers to have both SOC and ISO 27701 certifications to meet their specific security and privacy needs.
What benefits do SOC 2 compliance and ISO 27701 certification give to clients outsourcing their technology requirements to iTech
When clients outsource their technology requirements to iTech, which holds both SOC 2 (Service Organization Controls) and ISO 27701 certifications, they enjoy the following 6 specific benefits related to data security and privacy:
1. Enhanced Data Security: American business clients can trust that their sensitive information and data are in safe hands, as iTech’s SOC certification ensures rigorous controls are in place to safeguard data from unauthorized access and breaches.
2. Privacy Assurance: With ISO 27701 certification, iTech demonstrates a strong commitment to managing privacy information. Clients can rest assured that personal data and privacy rights are protected in compliance with global privacy standards.
3. Transparency: Both certifications provide clients with detailed insights into iTech’s control environment and privacy management systems, fostering transparency and trust in data handling processes.
4. Risk Mitigation: By partnering with iTech, clients reduce the risk of data breaches and security incidents, as SOC 2 and ISO 27701 certifications ensure a proactive approach to risk mitigation and compliance with privacy regulations.
5. Compliance with Regulatory Requirements: Many industries have stringent data protection regulations, such as GDPR. Clients benefit from iTech’s adherence to ISO 27701, as it ensures compliance with these regulations and eases their regulatory concerns.
6. Competitive Advantage: Clients can use iTech’s certifications as a valuable selling point, demonstrating their commitment to data security and privacy to their own customers and partners, ultimately enhancing their competitive edge.
Set up a demo with our senior team to understand iTech’s innovative AI solutions and Data Privacy guidelines.