NLP Applications: Real-World Impact Across Industries
Discover the power of NLP in business, turning unstructured text into insights, enhancing customer experiences, boosting efficiency, and enabling AI-driven decision-making across industries.
Discover the power of NLP in business, turning unstructured text into insights, enhancing customer experiences, boosting efficiency, and enabling AI-driven decision-making across industries.

Learn how AI helps manufacturers predict equipment failures by analyzing sensor data, reducing unplanned downtime, improving safety, and optimizing maintenance for better efficiency.

Discover how AI transforms mortgage lending by automating early-stage document verification for faster, smarter, and more reliable loan processing.

Discover 25 must-have features for Android apps, from AI personalization to secure payments. Enhance user experience, boost engagement, and ensure success with cutting-edge technology and design.

AI for Law Firms: Discover how AI is transforming paralegal work by automating legal research, document review, and compliance tracking. Learn how law firms can boost efficiency, reduce burnout, and stay competitive with AI-powered tools.

Discover how EDI transforms carrier operations by automating document exchange, reducing errors, and enhancing efficiency. Learn about modern EDI solutions, real-time tracking, and cost-saving integrations for scalable, compliant logistics management.
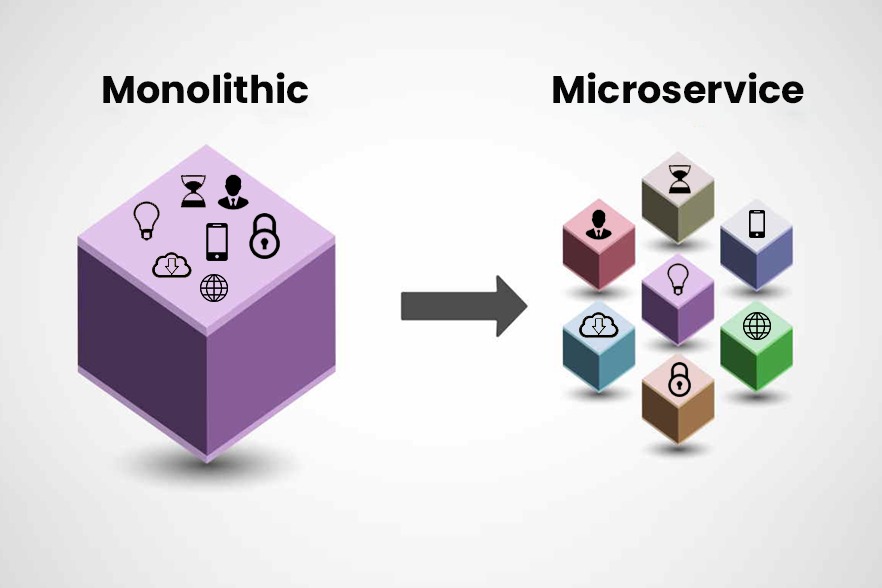
When too many people are working on a single tightly coupled codebase, as is normal in monolithic applications, bottlenecks are a usual challenge together with reliability and scaling problems. This
Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatu
Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo con
2nd Floor, Unipunch Pride, #40, 2nd Main Road, Ambattur Industrial Estate, Chennai-600 058, Tamil Nadu.
Other Locations : Tirunelveli, Villuppuram, Hyderabad
16803 Dallas Parkway, Suite: 300 Addison, TX 75001.

iTech uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognizing you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.